Introduction
TholosCTF is a Capture The Flag (CTF) challenge consisting of multiple levels, each containing a flag. Each flag is in the format flag{...}.
This website is probably down since I created this for my final project.
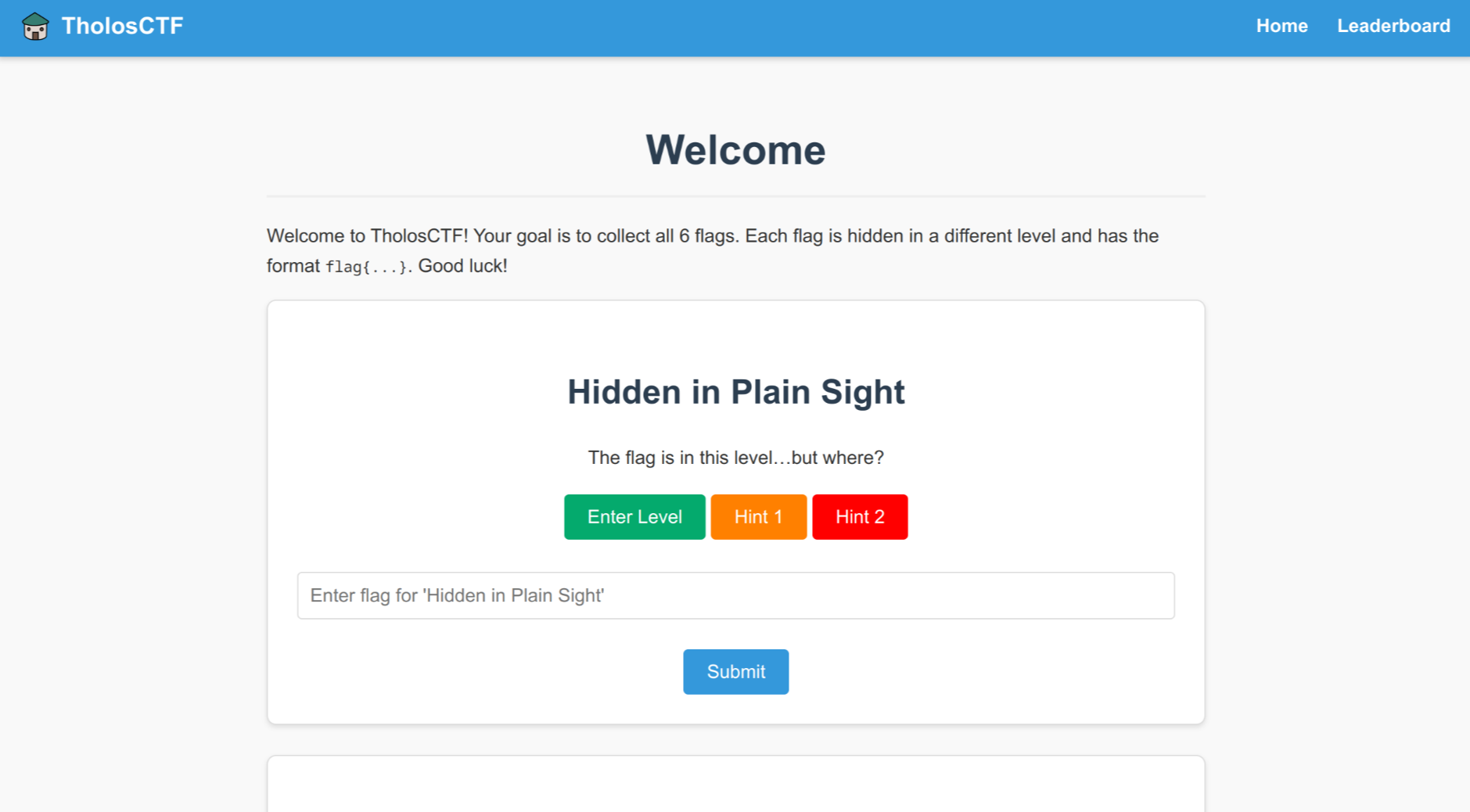
Here is what the page looks like:
Level Breakdown
I won't get too much into these levels, but I will provide the general setup and solution.
Level 1—Hidden in Plain Sight
The flag is written plainly in the HTML of the page and can be found when viewing the page source.
Level 2—CONK!
Upon inspection, there is JavaScript that decodes some string from base64 and saves it to a variable, and then prints to console.
The console will have the flag.
Level 3—Who Are You?
Upon inspecting the URL after clicking the button, the challenger should notice ?user=guest and change it to ?user=admin, which should reveal the flag.
Level 4—User Data
This level requires SQL injection of password field.
One possible injection is ' or 1=1;--. If entered into the username field and the password is random, the user should get a message saying that only admin can access the database. Then they should try "admin" as the username and the same injection for the password instead.
This should log the user into a page where they can view a table with usernames and passwords. The password of the admin user, when decoded from base64, will reveal the flag.
Level 5—Know Your Dinosaur
Upon visiting the page, the challenger will see a stegosaurus and some odd lyrics to some song.
Searching the song lyrics should tell them what kind of dinosaur it is, or they could recall from memory.
An astute challenger would connect the word "stegosaurus" to "steganography." The correct tool to use to extract the flag from the image is steghide.
The alt text of the image should give a SHA256 hash of the password, which the challenger has to crack in order to extract the flag.
The following command will reveal the flag, where PASSWORD is replaced with the cracked hash:
steghide extract -sf dinosaur.jpg -p "PASSWORD"Level 6—Nothing
Being the hardest level, the user is greeted with a page with nothing important on it. The user has to use directory brute-force techniques in order to find the flag.
First, they have to find the encrypted flag flag.gpg. It's unlikely they will find it though, so it is more likely they find download.html and then click the button to download the file.
The tricky part is that every page has the word "nothing" on it, so if they use that to filter out "bad" pages, it will fail.
Now the hardest part comes: they have to find the password to decrypt the file. If one inspects the 404 page, they will notice a bogus NGINX version 20.69.4, which should alert them to something weird going on. Viewing the source will reveal the password in plain text.